5 More Things to Keep your Data Safe
Nextcloud has important security features you should know about!
Today’s blog highlights five Nextcloud features that provide the utmost security. Nextcloud provides its users with dozens of data privacy features, however we’re providing it to you in chunks.

Monitoring
To keep your files safe, you should know what is happening to them. Nextcloud has a number of ways that help users keep an eye on their files.
How to monitor your files with Nextcloud:
- Track file activity – Have a clear overview of changes like newly added or deleted files in shared folders, recent edits, downloads, new comments from other users or tags, and more!
- Add more monitoring capabilites with Nextcloud apps: Activities for shared file downloads which lets you trackdownloads of your shared files, and Quota Warning which sends notifications to users when they reached 85, 90 and 95% of their quota. See more in the Nextcloud App Store.
- The Server Information app allows admins to monitor the state and performance of a Nextcloud server installation. It shows some basic statistics and gives access to data through an API endpoint which enables it to connect to.
- Industry standard tools like Splunk, Nagios and openNMS. In fact, Splunk and openNMS have support for monitoring Nextcloud systems.
- Auditing Logs allow you to log data in the nextcloud.log file to not only monitor file handling and user management, but prevent against data loss too.
Read more about Nextcloud Monitoring.
Advanced Permissions
Advanced Permissions allow the user to configure permissions on the files they share.
There are several types of permission options that make your files more secure like:
- Setting permissions on a shared file to: read, create, edit, and / or upload.
- Watermarking confidential documents to make it harder to steal data
- Enabling a password protection or expiration date on a public file or folder
- File-Drop: option to hide the contents of a folder where people can upload files to
- Blocking downloads so the user can view and even edit the shared file(s), but not download them
With all of these features available, users can ensure their files are only accessed the way they want.
Machine learning based suspicious login detection
Introduced back in Nextcloud 16 by one of our developers, you can protect your account through machine learning, which increases security and productivity even beyond our brute-force protection and 2-factor authentification.
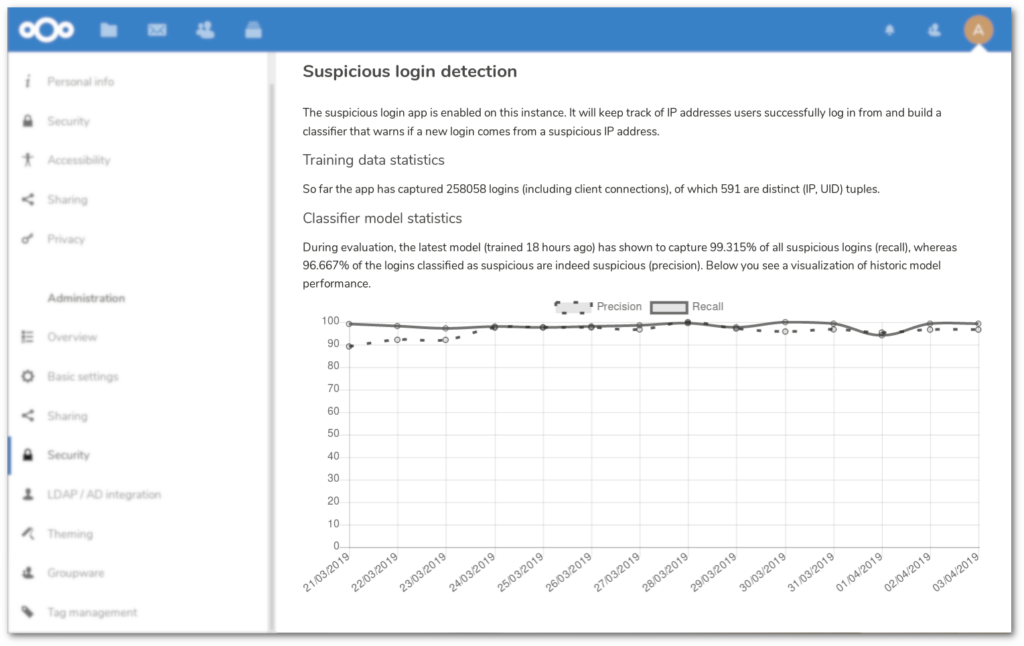
Suspicious Login Detection uses a locally trained neural network to detect attempts to login by malicious actors.
The way it works is that the app tracks a series of successful logins for a set period of time, and then uses the generated data to train a neural network. This network essentially learns the patterns of the user: at what time and from what location they usually log in. Once this trained model is formed, the system can detect any unusual or suspicious logins. For example, if a user typically logs into the office at 9AM, and suddenly there is a login from a different city at 11PM, something is off. When such a login is detected, the user gets a notification and can check the logs, potentially concluding in a password change by the user.
Note that Suspicious Login Detection trains and works with local data and does not send data anywhere else!
File Access Control
File Access Control is a feature that enables administrators to limit access to files in accordance to business and legal requirements.
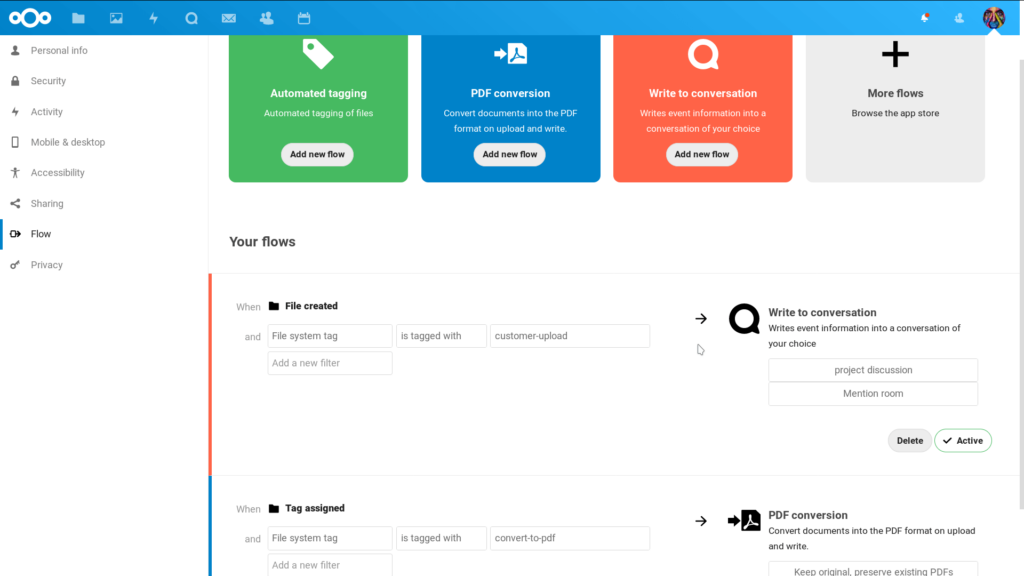
Rather than working on individual files, it creates a definition of rules that block file access, even if an individual user would have shared a file against company policy. File Access Control is configured using Flow, which can also allow an admin or user to perform automatic actions like file conversion, getting notified based on certain conditions, and more.
For example, a company’s HR department normally works with documents only they and management can see. The administrator in this case could create a rule or “flow” implementing the following rule: “PDF files – from the HR department – should not be accessible outside company IP ranges or from outside the HR department or management.” This means specifically that PDF files, from the HR department, outside company IP ranges, will be blocked.
You can set each specific filter as simple or complicated as you wish, as seen below:
If now for instance an HR employee would accidentally share a resume with the entire company, all is fine. When that link seems like it could be accessed outside of management, the HR teams, or outside the company IP range, the rule would kick in and block access to the file.
Another example deals with a more specific and complicated flow, seen below. You set up a flow that only blocks MIME file types of images, that are a member of the admin group, that have a file size less than 5 MB, and that matches a specific IPv4 IP address. If a file access request matches these credential rules, Nextcloud will block access to the file.
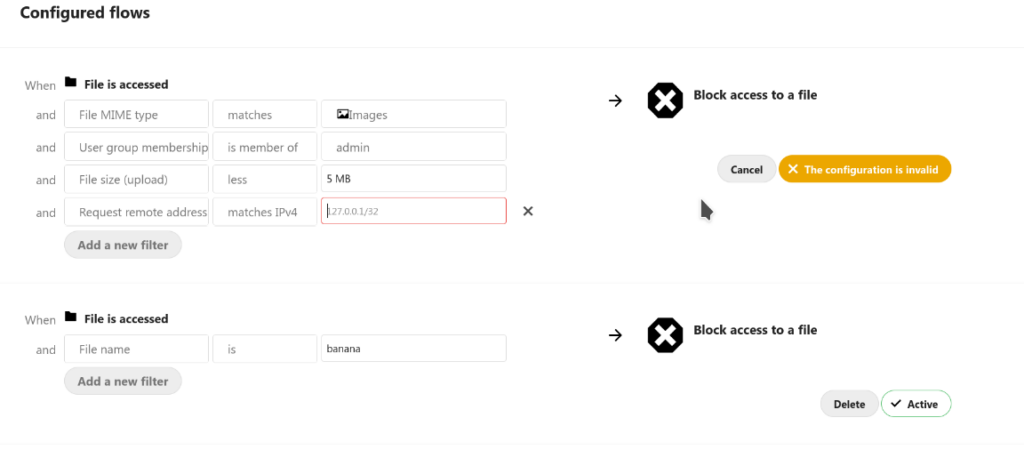
There are truly countless options to the flows you can configure which ultimately safeguard your day to day workflow and business.
Audits
Audits are important security and compliance measures that can be used by companies to identify problems, track and dissect the causes of security or data loss breaches, improve efficiency, and instill trust to their partners and customers. They are often legally required and thus it is important that a collaboration platform supports them.
City of Geneva Case Study
“After testing the solution in a Proof of Concept, it clearly appeared that Nextcloud was professionally developed and maintained. It was very stable and the security audit was excellent. It was prompt, professional and very efficient.”

Nextcloud supports an audit log which stores the activities of all users of the system, suitable for review in case this is needed.
Of course, as a company, we also have our own processes and code audits. Beyond that, customers do their own audits or work with third parties on auditing the Nextcloud code base.
One prime example is the code audit conducted by Swiss IT security firm Kyos for the City of Geneva, Switzerland. The results came back with flying colors and added an extra layer of security that could be deeply trusted from the core of the code.
Today’s post just highlighted 5, however we recently posted more security features that bring our users the reassurance regarding all things security.














